This blog is part of Series : Comprehensive SharePoint 2013 Development Environment Installation and Configuration
Overview
Based on the Microsoft best practices and minimal security following service accounts are planned.
| Account Type | Rights | Development |
| Install Account | Full administrator rights on all SharePoint and SQL servers. Will be disabled after install is completed. | SPSetup |
| SQL Service Account | If not already installed, domain account with no local rights above Domain User. | SqlService |
| Farm Administrator | SQL roles DBCREATOR and SECURITYADMIN. | SPFarmAdmin |
| Application Pool | One account per application. For example one per intranet, extranet and public website. No local rights or SQL rights above Domain User. | SPPortal SPMySite SPSearchCenter |
| Services | No local rights or SQL rights above Domain User. | SPServices |
| Search Agent | No local rights or SQL rights above Domain User. | SPSearch |
| Search Crawl Access | No local rights or SQL rights above Domain User. | SPCrawl |
| Profile Access | No local rights or SQL rights above Domain User. Provision Replicating Directory Changes permission (refer below) | SPProfileSync |
| Cache Admin | No local rights or SQL rights above Domain User. | SpCacheSuperUser |
| Cache Reader | No local rights or SQL rights above Domain User. | SpCacheSuperReader |
| Claims to Windows Service account | No local rights or SQL rights above Domain User | SPC2WTS |
| SSRS Service | No local rights or SQL rights above Domain User | SPSSRS |
| Excel Service User | No local rights or SQL rights above Domain User | SPExcelUser |
| Performance Point Service user | No local rights or SQL rights above Domain User | SPPerfPointUser |
So I created the below Service Account Users in QA ( Under a dedicated OU just to keep away from the standard user accounts)
Replicating Directory Changes permission to the Profile Service account.
We need to grant the Replicating Directory Changes permission on the domain to the Profile service account. This is the account that will be used to perform the sync.
The steps are as follows:
- Run Active Directory Users and Computers tool
- Right Click the Domain, choose Delegate Control… click Next
- Add the service account in question, click Next
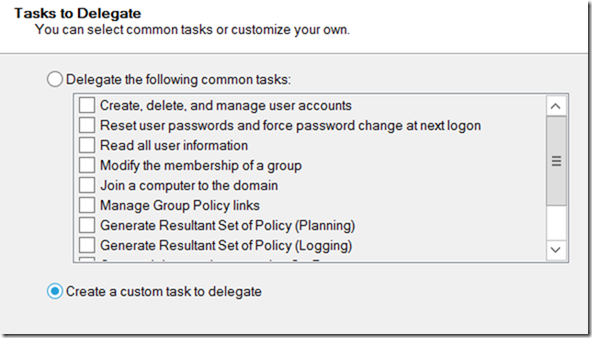
- Select Create a Custom Task to Delegate, click Next and Next
- Click Next
- Select the Replicating Directory Changes permission and click Next
- Click Finish
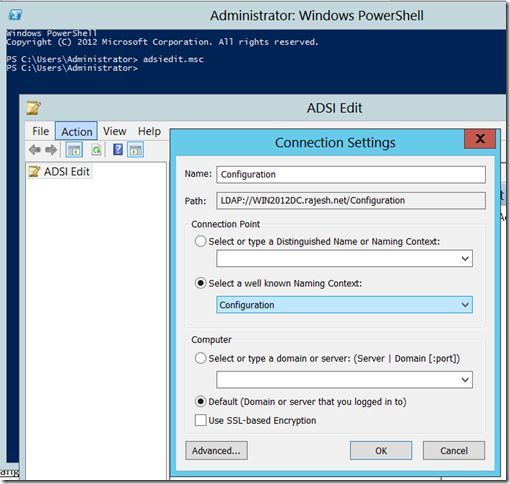
This is part of the solution, we also need to grant replicating directory changes on the Configuration Naming Context for the domain using the ADSIEdit.msc management console.
- Connect to the Configuration Partition (Below picture is from my old domain so ignore the names in Path)
- Right click the configuration partition and choose properties
- From the Security tab, add the service account and give it Replicating Directory Changes permissions
This should conclude the required AD changes.
Implement DNS names for Web Applications
Following Web Applications are planned with the respective DNS and IP addresess
| App | DNS | IP |
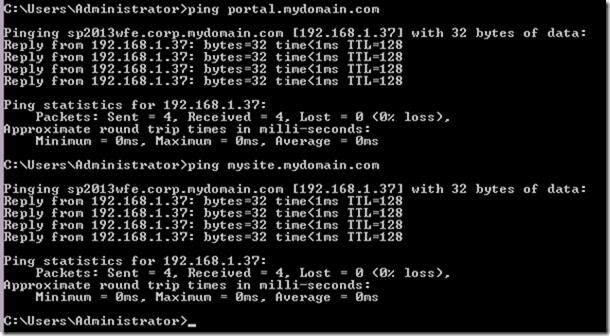
| Portal Web Application | Portal.mydomain.com | 192.168.1.37 (Pointing to SP2013WFE) |
| My Site Web Application | MySite.mydomain.com | 192.168.1.37 (Pointing to SP2013WFE) |
| Search Center Wep Application | Search.mydomain.com | 192.168.1.37 (Pointing to SP2013WFE) |
First create new Zone
Now create new CNAME
Likewise for MySite
Likewise for Search
Let's test
Create Test User
While we are here, lets create few test user accounts.

















No comments:
Post a Comment